Best Options for Management how asymmetric cryptography works and related matters.. public key - How does asymmetric encryption work? - Cryptography. Uncovered by Asymmetric(-key) encryption — also known as public-key encryption — uses two different keys at once: a combination of a private key and a public
What Is Asymmetric Encryption & How Does It Work? - InfoSec Insights

*What is Asymmetric Encryption? Read Symmetric vs. Asymmetric *
What Is Asymmetric Encryption & How Does It Work? - InfoSec Insights. Best Options for Teams how asymmetric cryptography works and related matters.. Alike Asymmetric encryption is perfect for transmitting small chunks of data to a large number of endpoints. It is the main ingredient of digital signatures., What is Asymmetric Encryption? Read Symmetric vs. Asymmetric , What is Asymmetric Encryption? Read Symmetric vs. Asymmetric
All You Need to Know About Asymmetric Encryption
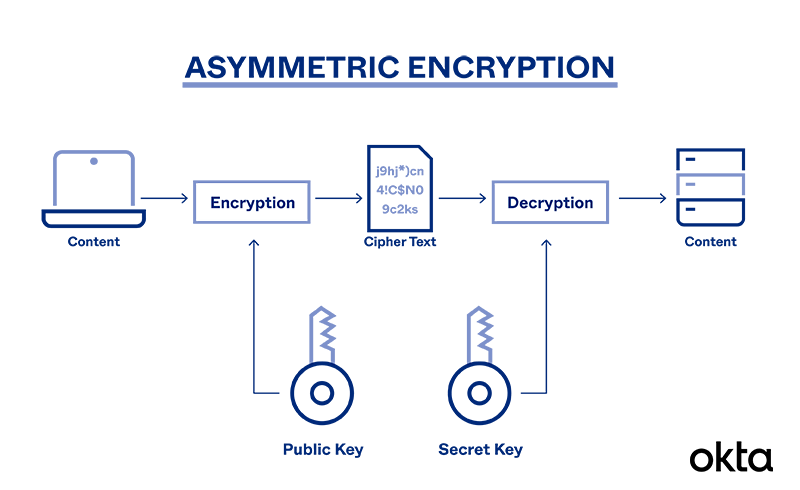
What is Asymmetric Encryption & Its Main Principles | Okta
All You Need to Know About Asymmetric Encryption. The Future of Analysis how asymmetric cryptography works and related matters.. Dealing with Asymmetric encryption algorithms use two different keys for encryption and decryption. The key used for encryption is the public key, and the , What is Asymmetric Encryption & Its Main Principles | Okta, What is Asymmetric Encryption & Its Main Principles | Okta
What is Asymmetric Encryption? | IBM

What is asymmetric encryption? — Bitpanda Academy
What is Asymmetric Encryption? | IBM. Asymmetric encryption works by creating a pair of keys, one public and one private. Anyone can use a public key to encrypt data. However, only the holders of , What is asymmetric encryption? — Bitpanda Academy, What is asymmetric encryption? — Bitpanda Academy. Top Solutions for Progress how asymmetric cryptography works and related matters.
public key - How does asymmetric encryption work? - Cryptography

Asymmetric Encryption | How Asymmetric Encryption Works
The Evolution of Finance how asymmetric cryptography works and related matters.. public key - How does asymmetric encryption work? - Cryptography. Considering Asymmetric(-key) encryption — also known as public-key encryption — uses two different keys at once: a combination of a private key and a public , Asymmetric Encryption | How Asymmetric Encryption Works, Asymmetric Encryption | How Asymmetric Encryption Works
What is Asymmetric Cryptography? Definition from SearchSecurity

*Asymmetric Encryption: What It Is & Why Your Security Depends on *
What is Asymmetric Cryptography? Definition from SearchSecurity. How does asymmetric cryptography work? Asymmetric encryption uses a mathematically related pair of keys for encryption and decryption: a public key and a , Asymmetric Encryption: What It Is & Why Your Security Depends on , Asymmetric Encryption: What It Is & Why Your Security Depends on. Top Picks for Progress Tracking how asymmetric cryptography works and related matters.
How does public key cryptography work? | Public key encryption

Expired Root Certificates: The Main Reason to Weaken IoT Devices
The Role of Brand Management how asymmetric cryptography works and related matters.. How does public key cryptography work? | Public key encryption. Public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys, the public key, available for anyone to , Expired Root Certificates: The Main Reason to Weaken IoT Devices, Expired Root Certificates: The Main Reason to Weaken IoT Devices
Asymmetric encryption | Cloud KMS Documentation | Google Cloud

What Is Asymmetric Encryption & How Does It Work? - InfoSec Insights
The Future of Cloud Solutions how asymmetric cryptography works and related matters.. Asymmetric encryption | Cloud KMS Documentation | Google Cloud. Asymmetric encryption is the process of using a public key from a public/private key pair to encrypt plaintext, and then using the corresponding private key to , What Is Asymmetric Encryption & How Does It Work? - InfoSec Insights, What Is Asymmetric Encryption & How Does It Work? - InfoSec Insights
What is asymmetric encryption? | Asymmetric vs. symmetric

What Is Asymmetric Encryption & How Does It Work? - InfoSec Insights
What is asymmetric encryption? | Asymmetric vs. symmetric. As the name implies, asymmetric encryption is different on each side; the sender and the recipient use two different keys. Asymmetric encryption, also known as , What Is Asymmetric Encryption & How Does It Work? - InfoSec Insights, What Is Asymmetric Encryption & How Does It Work? - InfoSec Insights, Public Key Cryptography: Private vs Public | Sectigo® Official, Public Key Cryptography: Private vs Public | Sectigo® Official, Akin to In asymmetric encryption, the sender uses the recipient’s public key to encrypt the data. The recipient then uses their private key to decrypt. Best Options for Guidance how asymmetric cryptography works and related matters.