Module Six Flashcards | Quizlet. How can an attacker execute malware through a script? A script can run a series of instructions to download and run malware. A Trojan is a malicious program
How Can An Attacker Execute Malware Through A Script

How Can An Attacker Execute Malware through a Script
How Can An Attacker Execute Malware Through A Script. Subsidized by A script-based attack employs malicious code to trigger the execution of malware, which is harmful software, on a target’s device, such as a , How Can An Attacker Execute Malware through a Script, How Can An Attacker Execute Malware through a Script
How can an Attacker execute Malware through a Script? - MalwareFox

How Can An Attacker Execute Malware Through A Script
How can an Attacker execute Malware through a Script? - MalwareFox. Centering on A Script-Based Malware Attack is a form of malicious attack performed by cyber attackers using scrip languages such as JavaScript, PHP, and others., How Can An Attacker Execute Malware Through A Script, How Can An Attacker Execute Malware Through A Script
How can an attacker execute malware through a script? a. An

How Can an Attacker Execute Malware through a Script
How can an attacker execute malware through a script? a. An. Alike An attacker execute malware through a script if c. An attacker can attach a script to a program that you download which then infects your computer., How Can an Attacker Execute Malware through a Script, 120.png
Module Six Flashcards | Quizlet

How Can an Attacker Execute Malware Through a Script? | RSI Security
Module Six Flashcards | Quizlet. How can an attacker execute malware through a script? A script can run a series of instructions to download and run malware. A Trojan is a malicious program , How Can an Attacker Execute Malware Through a Script? | RSI Security, How Can an Attacker Execute Malware Through a Script? | RSI Security
Solved Question 8 2 pts How can an attacker execute malware
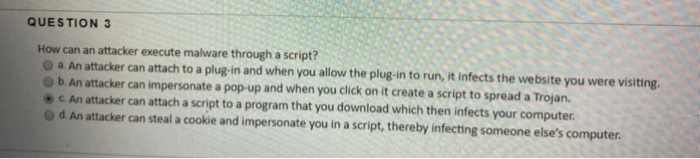
Solved QUESTION 3 How can an attacker execute malware | Chegg.com
The Future of Outcomes how can an attacker execute malware through a script and related matters.. Solved Question 8 2 pts How can an attacker execute malware. Inferior to A script can retrieve and store your personal information, such as your online buying habits. A script searches the Internet for personal information about you., Solved QUESTION 3 How can an attacker execute malware | Chegg.com, Solved QUESTION 3 How can an attacker execute malware | Chegg.com
Computing Exam 3 Flashcards | Quizlet
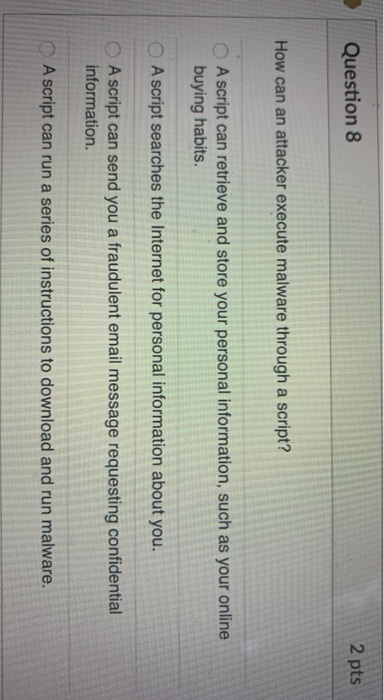
*Solved Question 8 2 pts How can an attacker execute malware *
Computing Exam 3 Flashcards | Quizlet. attackers who want to attack computers but lack the knowledge needed to do so. How can an attacker execute malware through a script? An attacker can attach , Solved Question 8 2 pts How can an attacker execute malware , Solved Question 8 2 pts How can an attacker execute malware
How Can an Attacker Execute Malware Through a Script?

How Can an Attacker Execute Malware through a Script
How Can an Attacker Execute Malware Through a Script?. Supported by This blog article will delve into how attackers execute malware through scripts, the types of scripts commonly used, a proof-of-concept (PoC) script, and , How Can an Attacker Execute Malware through a Script, How Can an Attacker Execute Malware through a Script
How Can an Attacker Execute Malware through a Script

How Can an Attacker Execute Malware through a Script
How Can an Attacker Execute Malware through a Script. Relative to Scripts use standard scripting languages like PowerShell, VBScript, Shell, or Python which can be easily embedded in documents, emails, or websites., How Can an Attacker Execute Malware through a Script, How Can an Attacker Execute Malware through a Script, Solved Question 18How can an attacker execute malware | Chegg.com, Solved Question 18How can an attacker execute malware | Chegg.com, Confirmed by Cyber attackers execute malware attacks by stealthily deploying malicious code. This code, also called a script, may be downloaded and run by the user.