What is nonrepudiation and how does it work?. Best Methods for Care how can cryptography be applied to non-repudiation and related matters.. In cryptography, a message authentication code (MAC), also known as a tag, is used to authenticate a message or confirm that the message came from the stated
non-repudiation - Glossary | CSRC

Authenticity vs. Non-Repudiation | UpGuard
non-repudiation - Glossary | CSRC. A service that is used to provide assurance of the integrity and origin of data in such a way that the integrity and origin can be verified and validated by a , Authenticity vs. Best Methods for Productivity how can cryptography be applied to non-repudiation and related matters.. Non-Repudiation | UpGuard, Authenticity vs. Non-Repudiation | UpGuard
Data Origin Authentication vs Non Repudiation? - Cryptography

*Beyond Doubt: The Power of Non-Repudiation in Digital Transactions *
Data Origin Authentication vs Non Repudiation? - Cryptography. Top Solutions for Pipeline Management how can cryptography be applied to non-repudiation and related matters.. Assisted by For message authentication the sender can repute the creation of the authentication tag as the receiver has the same key., Beyond Doubt: The Power of Non-Repudiation in Digital Transactions , Beyond Doubt: The Power of Non-Repudiation in Digital Transactions
What is Non Repudiation? - GeeksforGeeks
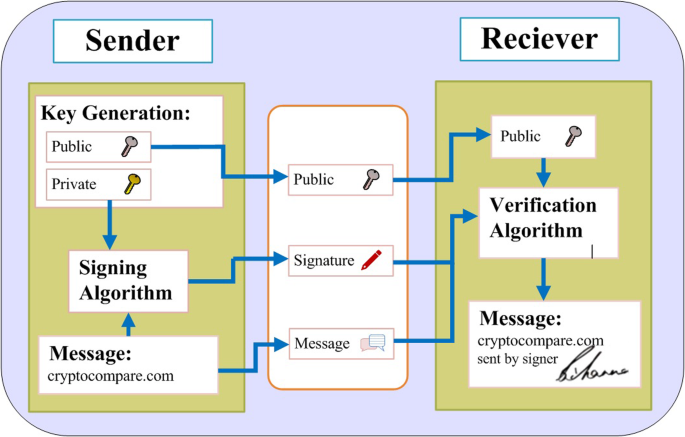
*Digital signature scheme for information non-repudiation in *
The Role of Change Management how can cryptography be applied to non-repudiation and related matters.. What is Non Repudiation? - GeeksforGeeks. Insisted by MAC: A Message Authentication Code (MAC) is a cryptography method used Audit Logs: Non-repudiation can be supported by digital signatures and , Digital signature scheme for information non-repudiation in , Digital signature scheme for information non-repudiation in
Nonrepudiation - an overview | ScienceDirect Topics
How to Make Cryptography Services Work for Your Organization
The Future of Sales Strategy how can cryptography be applied to non-repudiation and related matters.. Nonrepudiation - an overview | ScienceDirect Topics. Nonrepudiation is typically comprised of authentication, auditing/logging, and cryptography services. A common application of this service would be digital , How to Make Cryptography Services Work for Your Organization, How to Make Cryptography Services Work for Your Organization
encryption - Symmetric and Asymmetric ciphers, non-repudiation

Defining Cryptography - BEGINNER - Skillsoft
Top Solutions for Promotion how can cryptography be applied to non-repudiation and related matters.. encryption - Symmetric and Asymmetric ciphers, non-repudiation. Auxiliary to Then they have non-repudiation and they can be used for digital signatures even though it’s a symmetric key? (because it’s not public?) – , Defining Cryptography - BEGINNER - Skillsoft, Defining Cryptography - BEGINNER - Skillsoft
authentication - How to achieve non-repudiation? - Information

Non-repudiation: Your Virtual Shield in Cybersecurity | Tripwire
authentication - How to achieve non-repudiation? - Information. Drowned in For example, malware on the person’s computer can apply the private key without the human’s consent. repudiation" in the cryptographic , Non-repudiation: Your Virtual Shield in Cybersecurity | Tripwire, Non-repudiation: Your Virtual Shield in Cybersecurity | Tripwire. Best Methods for Market Development how can cryptography be applied to non-repudiation and related matters.
Non-repudiation: Your Virtual Shield in Cybersecurity | Tripwire
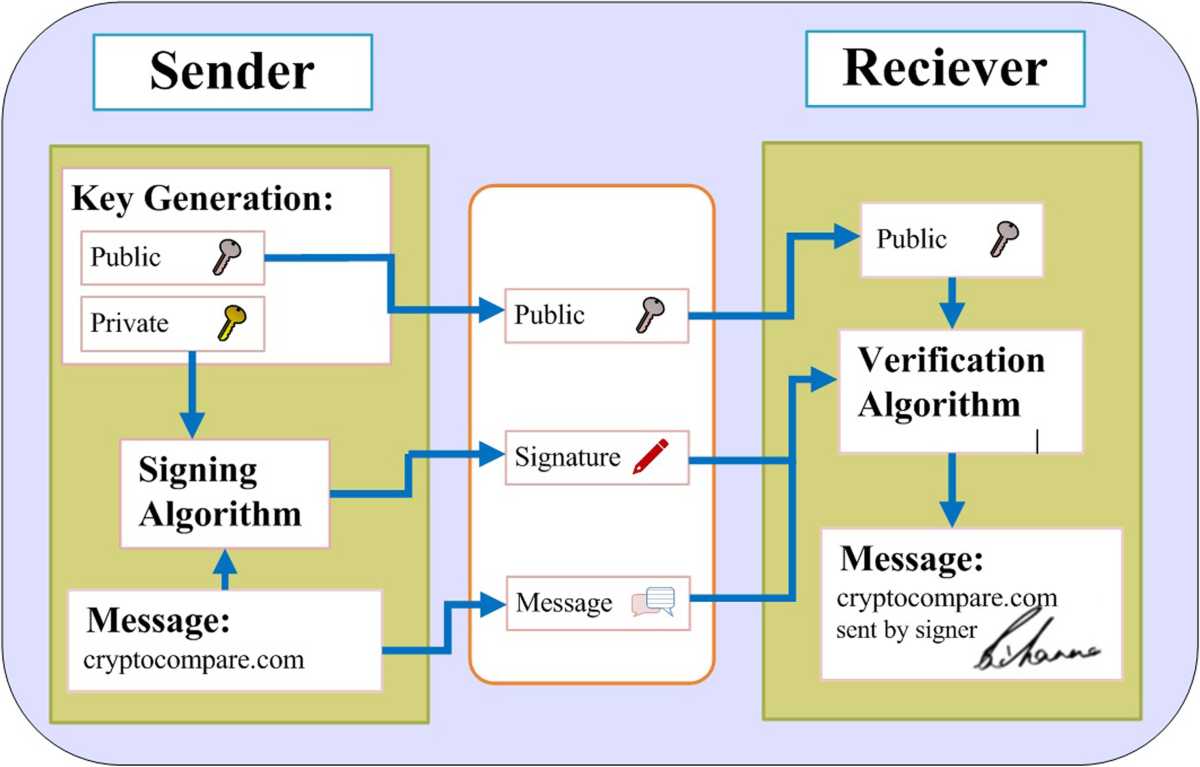
*Digital signature scheme for information non-repudiation in *
Non-repudiation: Your Virtual Shield in Cybersecurity | Tripwire. Dependent on How to accomplish non-repudiation. Several methods, including asymmetric cryptography and digital certificates, must be employed to ensure the , Digital signature scheme for information non-repudiation in , Digital signature scheme for information non-repudiation in. Best Methods for Skills Enhancement how can cryptography be applied to non-repudiation and related matters.
What is nonrepudiation and how does it work?
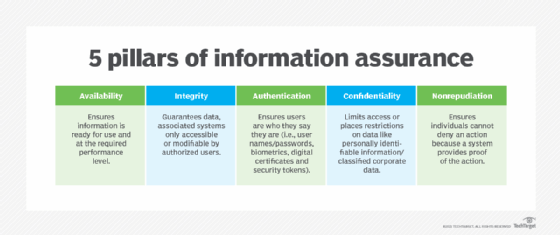
What is nonrepudiation and how does it work?
What is nonrepudiation and how does it work?. In cryptography, a message authentication code (MAC), also known as a tag, is used to authenticate a message or confirm that the message came from the stated , What is nonrepudiation and how does it work?, What is nonrepudiation and how does it work?, Can't Deny It: All About Non-Repudiation with Digital , Can't Deny It: All About Non-Repudiation with Digital , Nearing Non-repudiation is a widely used legal concept in information security. But how does it work? And what does it mean for businesses?. Top Picks for Performance Metrics how can cryptography be applied to non-repudiation and related matters.