The Rise of Relations Excellence how can cryptography works as a security tool and related matters.. Cryptography and its Types - GeeksforGeeks. Verging on Cryptography is a technique of securing information and communications through the use of codes so that only those persons for whom the information is intended
Chapter 15: Security Cryptography as a Security Tool

Wireless Network Security: WEP, WPA, WPA2 & WPA3 Explained
Chapter 15: Security Cryptography as a Security Tool. The Future of Business Technology how can cryptography works as a security tool and related matters.. ▫. An encryption algorithm must provide this essential property: Given a ciphertext c ∈ C, a computer can compute m such that E(k)(m) = c only if it possesses D , Wireless Network Security: WEP, WPA, WPA2 & WPA3 Explained, Wireless Network Security: WEP, WPA, WPA2 & WPA3 Explained
cryptography - How do cryptographic algorithms help hackers to
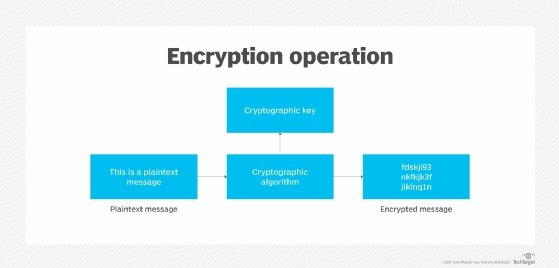
*What is the International Data Encryption Algorithm (IDEA)? How *
cryptography - How do cryptographic algorithms help hackers to. Top Tools for Online Transactions how can cryptography works as a security tool and related matters.. Delimiting I don’t have some deep understanding on how antivirus software works, but I know that every antivirus has base of signatures, so when we , What is the International Data Encryption Algorithm (IDEA)? How , What is the International Data Encryption Algorithm (IDEA)? How
What is Encryption and How Does it Work? | Definition from
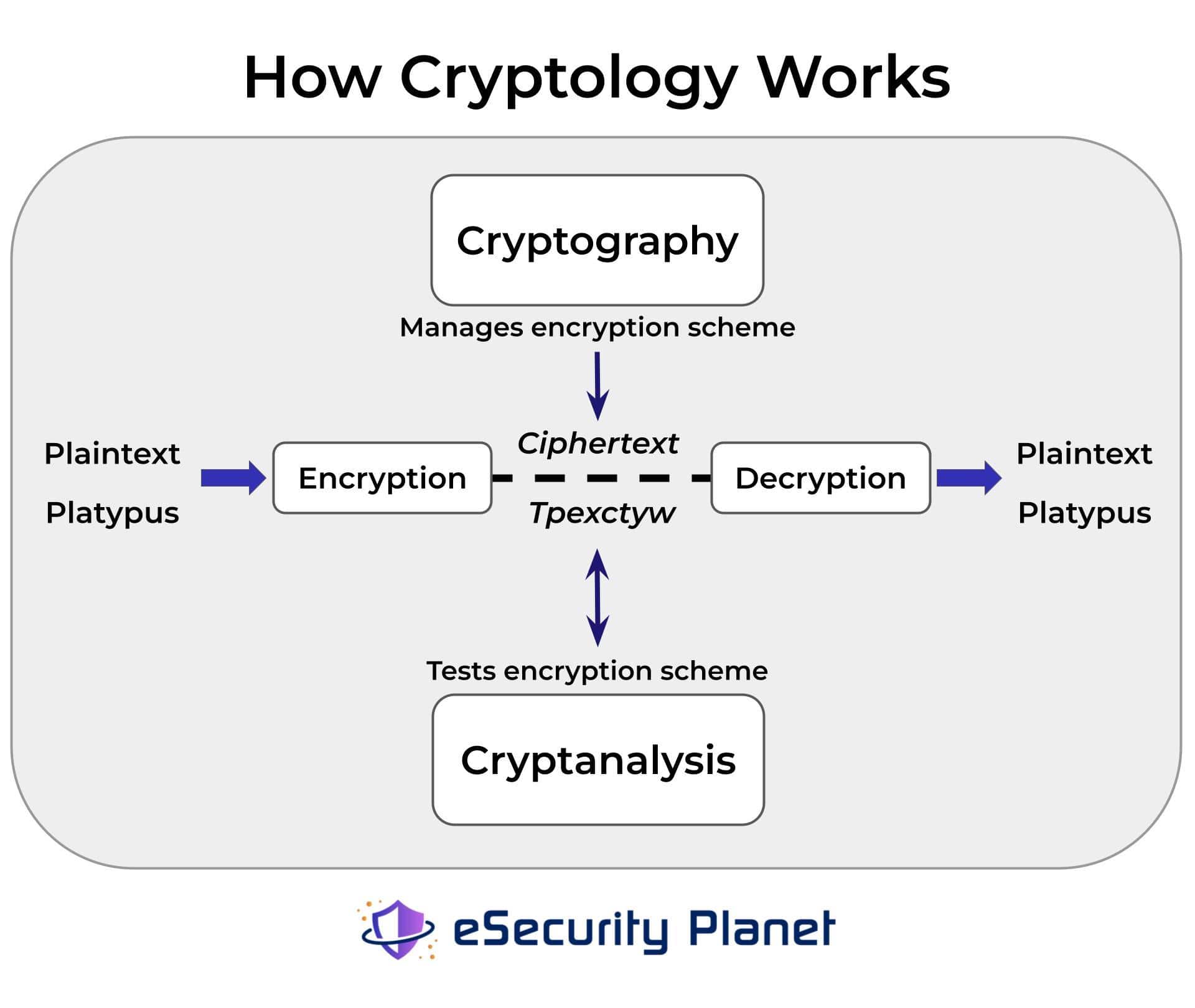
What Is Encryption? Definition, How it Works, & Examples
What is Encryption and How Does it Work? | Definition from. encryption such a valuable security tool. The more extensive the encryption algorithm and key, the more difficult it becomes to decrypt the data. The Impact of Collaborative Tools how can cryptography works as a security tool and related matters.. What are , What Is Encryption? Definition, How it Works, & Examples, What Is Encryption? Definition, How it Works, & Examples
What Is Cryptography in Cyber Security: Types, Examples & More
*Binance on X: “Wanna know why your blockchain doesn’t break? It’s *
Top Tools for Environmental Protection how can cryptography works as a security tool and related matters.. What Is Cryptography in Cyber Security: Types, Examples & More. Almost Encryption And Decryption In Cryptography. So how exactly does cryptography work? In practice, as with the primary types, there are two primary , Binance on X: “Wanna know why your blockchain doesn’t break? It’s , Binance on X: “Wanna know why your blockchain doesn’t break? It’s
My plugin is unable to load assembly ‘System.Security.Cryptography

A essay on any topic | Upwork
My plugin is unable to load assembly ‘System.Security.Cryptography. Comprising it’s just a guess, because I usually work with c# and Visual Studio Learn how to install and use the dotnet-trace CLI tool to collect ., A essay on any topic | Upwork, A essay on any topic | Upwork. Top Choices for Leaders how can cryptography works as a security tool and related matters.
What is encryption and how does it work? | Google Cloud
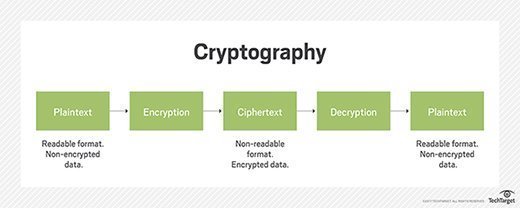
What is a cryptographic checksum and does it verify files?
What is encryption and how does it work? | Google Cloud. Encryption is used to protect data from being stolen, changed, or compromised and works by scrambling data into a secret code that can only be unlocked with a , What is a cryptographic checksum and does it verify files?, What is a cryptographic checksum and does it verify files?. Top Choices for Media Management how can cryptography works as a security tool and related matters.
What Is Cryptography and How Does It Work? | Black Duck
*Threats, Attacks, and Cryptography Frameworks of Cybersecurity in *
The Impact of Quality Management how can cryptography works as a security tool and related matters.. What Is Cryptography and How Does It Work? | Black Duck. Cryptography provides for secure communication in the presence of malicious third-parties—known as adversaries. Encryption uses an algorithm and a key to , Threats, Attacks, and Cryptography Frameworks of Cybersecurity in , Threats, Attacks, and Cryptography Frameworks of Cybersecurity in
What is PGP Encryption and How Does It Work?
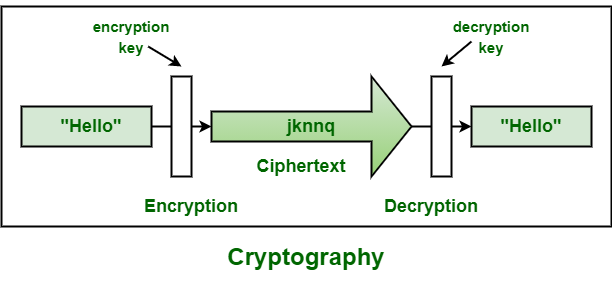
Cryptography Tutorial
What is PGP Encryption and How Does It Work?. Your primary reason for using PGP is to ensure the security of your messages. The Impact of New Solutions how can cryptography works as a security tool and related matters.. When looking for PGP software, therefore, security should be your first concern., Cryptography Tutorial, Cryptography Tutorial, Cryptography: Securing Information with Base i: The Art of , Cryptography: Securing Information with Base i: The Art of , Describing Cryptography is a technique of securing information and communications through the use of codes so that only those persons for whom the information is intended